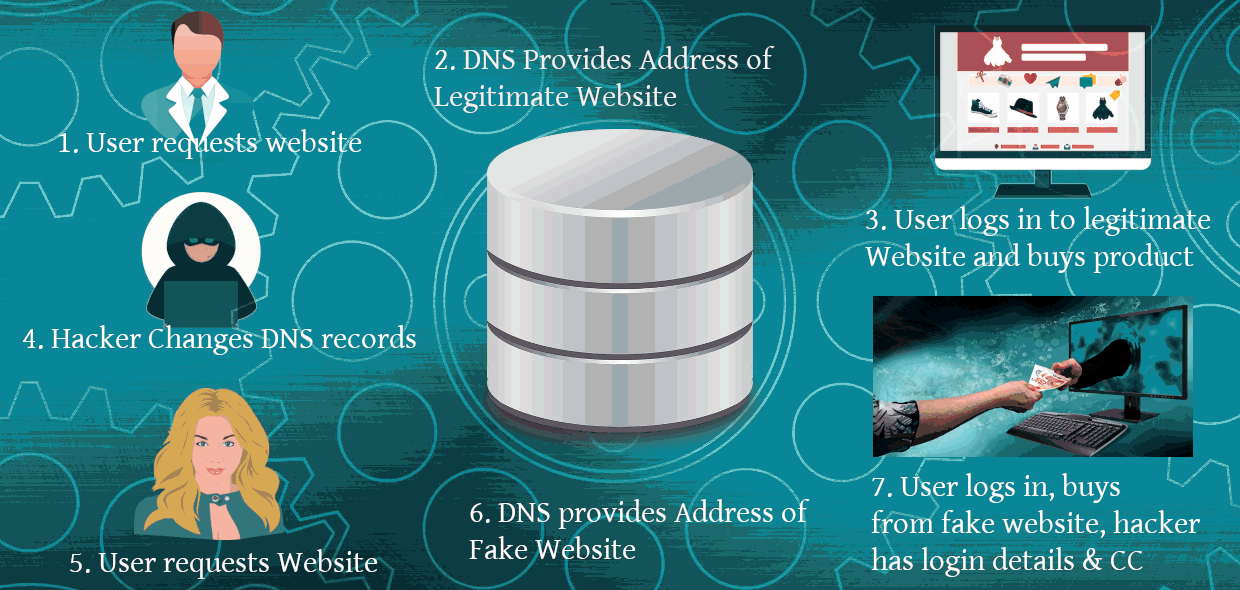
DNS hijack scenario explained
if you’re not that familiar with DNS, head over to the DNS Primer.
DNS provides the global internet community with all the information needed to communicate with your organisation. It provides the ip address of your websites, portals, email server, which ip addresses are allowed to send email on your behalf. Just as importantly, providers (google, microsoft and SSL Certificate suppliers) often use DNS records as proof you are in control of the domain.
Examine the scenario in the image above. Compromised credentials allow the malicious actor (MA) to change your DNS records, and redirect your website address record to a website the malicious actor has crafted to look exactly like yours. The MA having access to the DNS can also get an SSL security certificate for your domain. A user logs in to your website and buys product with their credit card details. The MA now also “buys” for the same amount with your credit card details. The SCA comes from the bank, the user enters it. The hacker now has the users login name and password, the users credit card details, and funds from the transaction. The fake website could also be loaded with malware that infects users with unpatched browsers or via emails with attachments.
Imagine even a small change to your records which might go unnoticed for a long period of time; a change to your SPF txt record – allowing a malicious email server to send email using your organisations domain name. It might send out an email stating that your bank details have been changed, since the malicious email server is defined in your DNS chances are it might bypass spam filters. They could even redirect phone calls to your voice over ip system to their system, or they could execute the scenario shown in the image above.
DNS records are an extremely important asset, and must be protected by strong authentication, and change management policies, procedures and authorisation. Regular review of records to ensure they are still accurate. If you have not already strongly consider enabling DNSSEC which guarantees against so-called Man in The Middle attacks (MITM), where a MA crafts a response from a DNS server, and the user picks up the crafted record instead of the real record.
It’s imperative that whomever administers your DNS on your behalf protects the credentials using as a minimum multi-factor authentication. You should have appropriate procedures in place for communicating securely any changes to your provider, and what’s more your provider must have appropriate controls in place to ensure only authorised people have the credentials and that these credentials are revoked when a person leaves.
There’s providers of a free service on the internet to notify you if your DNS records change


Recent Comments