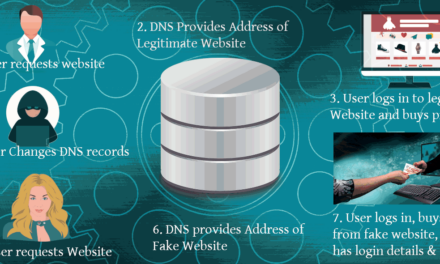
Encrypted password disclosed in a breach isn’t a concern because its encrypted. with a one way hash – meaning it can’t be decrypted – so that’s fine right?

Unfortunately there’s a technique called the rainbow table attack.
Encrypted password disclosed
it might be an emergencyIt turns out that more than one password can generate the same hash, and someone has taken the time to generate millions of hashes and their associated passwords. So in effect a malicious actor could look up your disclosed password hash, and find a password that generates the same hash and use that to login to your account.
There’s a simple defence that software engineers should use and that’s a password salt, so you combine the salt and encrypt the given password, and that generates the hash then it’s much more difficult to successfully execute a rainbow attack, since an attacker won’t know the salt.
As a user through you don’t know which applications use and which don’t use a salt. As an example windows LMNT does not use a salt.
Security researchers would suggest that rainbow techniques have been surpassed by modern password cracking methodogies.; most attackers now use farms of graphics processor units (GPUs).
Scary Password Facts – It’s a fact that approximately 65% of users reuse passwords typically as many as 14 times. Compromised passwords are the cause of 81% of all breaches.
But since you can’t be sure you need to assume that any encrypted password disclosure means your password has been disclosed, if you use that same password on many different systems you need to change them all and now.
A server running 8 GPUs (costing about 1600 euro) can crack any 8 character password in 48 minutes.
Hackers also keep and share tables of the most common passwords, and typically use these first before resorting to brute force attacks.
What can you and your organisation do to protect against password disclosure?
Enforce a policy on internal systems so that users must have a 12 character or more password with a mix of upper and lower case characters, numbers and special characters, where old passwords cannot be re-used. Passwords which relate to names, places, people, dates of birth should not be permitted.
Ensure that all users have a password manager installed so they use unique passwords on very site/applcation and do not have to remember them,
Enforce multi-factor authentication using an authenticator app (rather than SMS messages) on all internal systems, and educate users to use it when they register on any external platform or website
Even better still use password less authentication
Educate your users in security awareness – always educate them in one to one or group sessions but never via a newsletter or banner.
Frequently test your security posture by sending test social engineering/phishing/spear phishing attack campaigns to your users and educate those that respond,
Sign up to haveibeenpwned.com domain search – it’s free and will email you if an email address in your organisation has been the subject of a disclosure.
Passwordless Authentication
Passwordless Authentication uses biometrics, an authentication app on your mobile phone, a magiclink, or something you have like a security key or a combination of these. Not only is it not possible to disclose a password you don’t know, but if you don’t have one you can’t forget it. Appproximately 50% of IT professionals surveyed by could not complete a transaction because they forgot their password,
Magiclnks invoive entering your email address, the application sends a link to the email address and clicking on the onetime link. You need to have followed email best practices before you even consider this technique. If your email system is already compromised implementing magiclinks can made a bad situation worse.
Automated and human checks need to be regularly performed to ensure your organisations email system hasn’t been breached.
There are third party solutions which are certified to integrate with most operating systems and platforms. Examples include Auth0, Yubico


Recent Comments