
Sadly I can’t take credit for the title of the blog post, it’s from Kevin Mandia, who’s COO at Fireeye
It’s going to happen
The more prepared you are for a breach, the less time & money it will take your business to recover. Compromises affect not just the bottom line (even a small breach of email addresses can cost 100K or so, and a major breach many times that amount), but potentially the reputation and existence of your organisation. So a well thought out plan is imperative, you also need to examine the implications of a compromise at your IT or business systems provider or even your bank. So-called supply chain attacks are on the rise, so you need to ensure that your entire business eco-system is included in planning.
The Human Factor
It’s a fact that most breaches are caused by human factors, either a person accidentally disclosing their credentials to a malicious actor, or failing to patch an operating system or firmware. So educating your staff in security awareness regularly is key to keeping your systems secure. There’s an old Russian proverb “Trust but Verify” – so you trust your IT provider to keep your systems up to date and configured with the latest techniques and features to keep your systems secure, but do you ever verify that’s the case – the answer for most companies is no, but you should. Furthermore you should conduct regular automated test phishing/social engineering campaigns to test if your staff education is effective or whether some staff need further education.
An imperative is to implement multi-factor authentication across all systems, usernames and password no matter how strong are no longer enough. Username, Password, Device specific Pin, Biometrics, Phone App, and the adoption of least privilege necessary will all assist in keeping your IT ecosystem secure, but they are not enough on their own. SMS messaging for multi-factor authentication should be avoided – your mobile number may be at the end of all your emails – and that’s all the information an attacker needs to conduct a campaign against your credentials.
Nation/state proxy APT groups
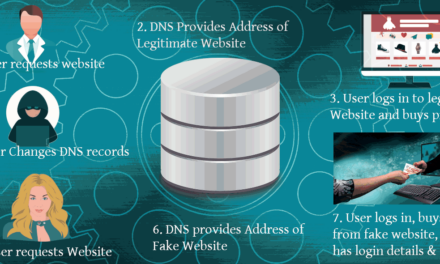
Nowadays certain governments are involved in revenue generation from ransomware type attacks, industrial & military espionage, and economic disruption. Crimunal gangs are demanding ransoms in some cases of more than $10m. A recent attack (the Solarwinds attack which purportedly infiltrated US Government, Defense, and the UK Govenment) was analysed by Microsoft, they determined that over 1000 programmers were involved. State sponsored proxy groups have huge resources, and develop so-called zero day exploits (where the developer of the software is unaware of the exploit), and practice techniques designed to avoid detection by scanning software. So you’re internet protection sofware on its own is not going to protect you. Zero day exploits detected in 2020 affected Firefox, Internet Explorer, Chrome, Trend Micro Office Scan, Windows 10, Sophos XG firewall, and i’ll bet that you’re business uses at least one of these products. Recently the Solarwinds attack has been determined to have been caused by either a brute force password attack, social engineering (Phishing), or a zero day exploit
Make no bones about it, these groups are extremely sophisticated, and organised.
Implement a Security Framework
Ensure cybersecurity is a conversation occurring at the highest levels of executive leadership. Cybersecurity is not an IT problem, it is an enterprise-wide risk management topic that requires attention.
Firstly, have a look at getting Cyber Essentials certification, its a UK standard (currently no European equivalent exists), that will give the non technical a idea of where the organisation is at. It’s a self certification and costs 300 GBP + Vat. It looks at 5 areas Boundary Firewalls and Internet Gateways Secure Configuration, User Access Control, Malware Protection and Patch Management. For some organisations that might suffice.
Adopt some form of globally recognised security standards or benchmark (ISO27001 or CIS) and score your systems against the benchmark. That will deliver a to-do list. Create a plan based on risk.
Get Certified
Once the plan is complete, a technical hands-on audit by a 3rd party accredited body to ensure that you & your security partners haven’t missed anything, and you’ll get Cyber Essentials Plus or ISO27001 accreditation.
Remote Working
Just because your IT Provider implemented a solution for remote working doesn’t mean its secure.
You really need to think if you are allowing employees to access systems in the Bring your own device (BYOD) model, its extremely risky, and do not forget mobile phones can be compromised and used as an attack vector. It’s easy for a remote worker to get a phone call from supposed IT support or IT security and disclose information, or their PC/laptop or mobile phone could be compromised.
THE AI Approach to security
In addition to following best practice, the answer is a paradigm shift in detection, rather than purely scan files for known malware signatures in isolation; protection systems need to deploy AI to constantly learn what is normal behaviour in your computing environment and flag abnormal behaviour. crowdstrike and sentinelone are probably the current the leaders in this field.
Defence in Depth
A defense in depth approach is a multi-layered solution using differing technologies, processes, practices, techniques and soluton providers o make it more difficult for malicious actors to penetrate your systems. As ever, though humans will remain the weakest link. The more critical or confidential the more protection layers you would need to deploy. An opposing principle is simplicity in security – arguing that complex architectures create gaps.

Recent Comments