A malicious actor who gains control of your DNS records can wreak untold damage on your organisation, so ensure that whomever administers it on your behalf has appropriate security controls in place – as a minimum multi-factor authentication
You hear the term DNS alot, but exactly what is it, what does it do?
DNS stands for domain name service. Devices on the internet can communicate globally (and in space) because they have a unique address – called an IP address. An ip address (IPV4). looks something like this 91.198.174.192. There’s not too many people who are going to remember that. The clever people at the Internet Engineering Task Force, came up with the concept of domain names which are human readable, and more important human rememberable. DNS became the engine which translates domain names into IP addresses. Now 91.198.174.192 becomes wikipedia.org and DNS does the translation.
It does a little more than that though it also tells your email client what server handles email for the domain using a slightly different record (MX – mail exchange), and similatly for voice over IP (VOIP) using SRV records. Sometimes a service needs more information than just an IP address, so DNS implements a TXT record type which can be used to pass information about that domain.
What do DNS records look like?
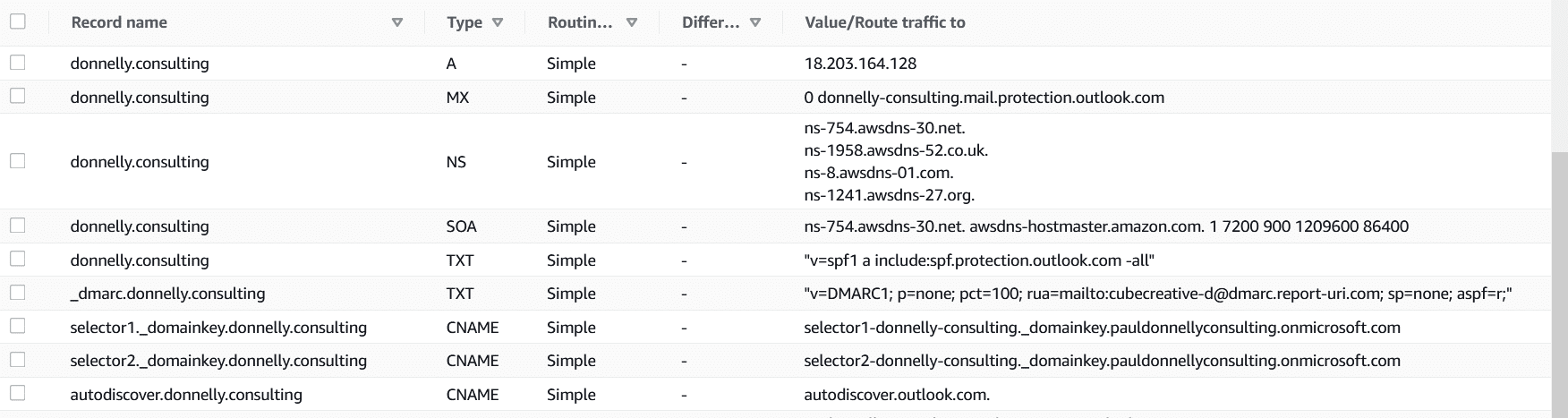
The First record is an A (address) record, it tells DNS to translate donnelly.consulting into the ip address 18.203.164.128
The second record is an MX (mail exchange record), it tells DNS that this is the server which handles email for the domain donnelly.consulting. You’ll notice that there’s a zero 0 before the server name, thats the priority 0 is the highest priority 100 the least. It’s possible to have more than one MX record, if you have say two email servers handling email for your domain, each with the same or different priorities. It’ll try to exchange email with the highest priority server(s), first if it fails it will try the next highest priority server.
NS (name servers) are the servers which handle the DNS records for this domain, we have four in our case. If one is not available a DNS request is routed to the second and so on. If you are a large organisation, you would usually use DNS servers from two or more different providers. We have seen the case where huge companies used only one provider which crashed.
SOA (source of authority). In the case where there is a conflict between the results received from nameservers which is the definitive source of information for this domain.
TXT records – sometimes more information is required, TXT records permit passing of more information, or sometimes companies ask you to put information in a TXT record to prove you are the owner, or administrator of this domain.
CNAME records – permit aliases.
IP addresses explained
There’s two versions of IP addresses in use on the internet IPV4 (IP version 4), and IPV6 (version 6), version 5 was developed but never implemented since it was superceded by 6.
We’re going to explain here version 4, which is currently the mainstream version. An IP address is really a single 32bit number, but for readability it is split into 4 8bit (octet) numbers separated by a period (full stop to you and me). Each octet can hold numbers in the range from 0 to 255. So you get something like 192.168.10.1 (192 first octet, 168 second octet, 10 third octet, 1 fourth octet)
How many globally unique IP addresses are there?
Well you can calculate it 255 x 255 x 255 x 255 = 3,706,452,992 thats nearly 4 billion addresses, but it’s nowhere near enough. Consider each house with a ring doorbell, TV, CCTV cameras, fridge etc connected to the internet (so called Internet of things IOT). The Internet Engineering Task Force (IETF) who come up with the standards on which the internet relies, came up with ways of sharing internet addresses, hence you can have more than one domain being served by a single webserver, and something called Network address translation (NAT), which allows a company to have thousands of devices internally, but appear on the internet as a single IP Address. Now even thats breaking and the world is ever so slowly moving to IPV6 which will provide 3.4×1038
is there only one DNS server on the internet?
No you have to remember that the original internet was created to enable communications in a nuclear war, so it’s built with resilience from the original design up. There are millions of DNS servers.
How are DNS servers kept in sync?
DNS has a record type of NS (nameserver), it specifies that this particular nameserver is the Source of Authority for this domain. For resilience purposes you can and should have more than one nameserver listed itthe domain, they all sync together. It’s a tad more complicated than this but these nameservers upload any changes to the Root Nameserver for the top level domain name (.com, .ie, .co.uk, .edu, .consulting), when you query a DNS server for a translation, if it doesn’t have it in its cache, it queries the root nameserver, puts the response in its cache and responds. The issue is though that it has no way of knowing whether the response has been tampered with in transit or that it was actually the root server which provided the response. A further marker in the DNS record is the time to live (TTL). it specifies how long a DNS server can keep a record cached before it asks the root server for a refreshed record – in case its changed. It’s specified in seconds. So the larger the TTL the longer its going to take to fully propagate a change across the internet.
How many Root Nameservers are there?
There’s actually only 13 historically these were single machines, but now they are server clusters. The reason there isn’t more is down to limitations in IPv4.
How do I know that the DNS server I am using is legitimate?
Normally, the internet service provider (Virgin, Eir, Vodafone, Magnet, etc) leases an IP address to your device when you connect to it. It also sends its preferred DNS server, however, there’s nothing to stop you defining your favourite server (google’s public DNS server etc). But here’s the rub, you pop into your local coffee shop, and connect to the WIFI.
It’s the WIFI access point in the shop which allocates the IP address and DNS server – only you’ve connected to a malicious actors WIFI placed in a rucksack, and they are in control of the DNS server, and can manipulate the IP address it returns – this is called the man in the middle attack vector (MITM). So if you are using a public wifi, always specify the DNS server to be used e.g. 8.8.8.8 or 8.8.4.4 which are googles public DNS servers.
Enter DNS Security Extensions (DNSSEC)
Engineers in the Internet Engineering Task Force (IETF), the organization responsible for the DNS protocol standards, long realized the lack of stronger authentication in DNS was a problem. Work on a solution began in the 1990s and the result was the DNSSEC Security Extensions (DNSSEC).
DNSSEC strengthens authentication in DNS using digital signatures based on public key cryptography. With DNSSEC, it’s not DNS queries and responses themselves that are cryptographically signed, but rather DNS data itself is signed by the owner of the data.


Recent Comments